Do you know what is the root cause of the majority of ransomware attacks? It is the error in the configurations in the systems and devices. This is according to Microsoft.
According to Microsoft, approximately 80% of the ransomware is due to network configuration errors.
What is Ransomware?
Ransomware is a malware (malicious software) or a computer virus. It is designed to deny the access to file(s) by the user in the system.
The ransomware attackers demand for the money in exchange of returning the access back to the user.
It’s like kidnapping or hijacking.
How ransomware works?
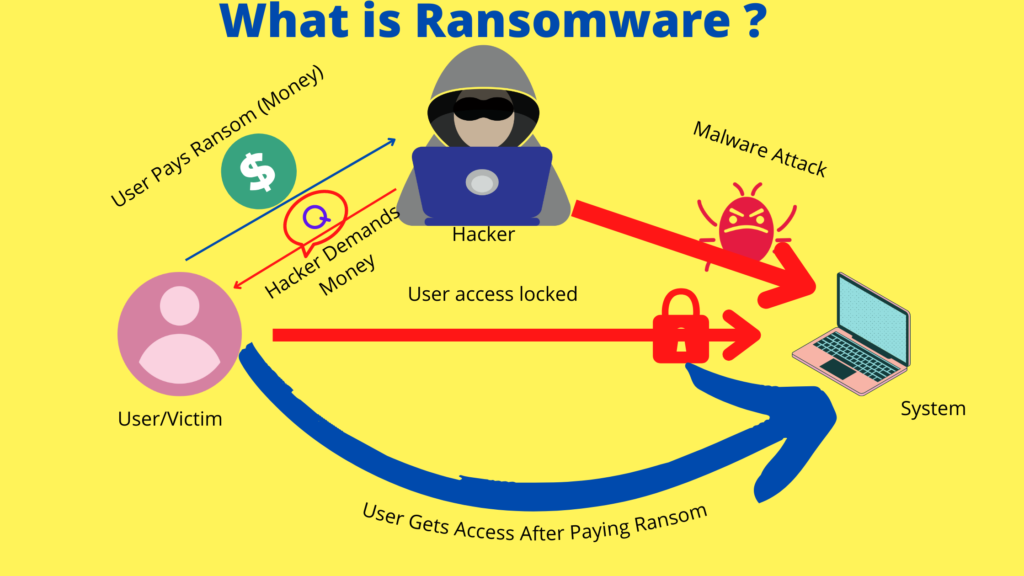
Let’s understand how ransomware works.
Assume that you get an email. The sender of the email looks like your friend.
In the email, it is asked to open the text file attached to it to get someone’s phone number.
You double click on that text file attached.
Done ! malware is installed on your system.
Now, malware is installed on your system by phishing.
It gains access to the file system/device or entire Operating system. This is based on the type of malware.
Having the access, the malware encrypts the files or Operating system.
This encryption blocks you from accessing files in the device infected.
Then the attacker demands ransom from you, the victim to decrypt or return the access to files/system.
Ransom can be demanded in terms of money or Crypto currency.
Which are the main forms of ransomwares?
On a high level, ransomwares are categorized in to 2 forms.
They are :
Locker Ransomware
Crypto Ransomware
Locker Ransomware
In this form of ransomware, normal functioning of the victim systems are locked by the hacker.
Example: You can edit the files, you can not move the files, etc.
Crypto Ransomware
In this form of ransomware, the hacker completely locks the file by encryption. The user can not access the files without decryption.
Ransomware As a Service
In recent days, attackers are relying on the tools and renting them for other attackers.
So developed ransomwares are made as a service.
Therefore there are a large number of attacks which are observed.
What is the root cause of ransomware attacks as per Microsoft?
Ransomware attacks involve decisions based on configurations of networks and differ for each victim even if the ransomware payload is the same.
Although each attack is different, Microsoft pointed out two key areas of risk exposure:
- Missing or misconfigured security products
- Legacy configurations in enterprise applications
How to Mitigate The Risks of Ransomware Attacks?
Some steps/measures suggested by Microsoft are :
- Like smoke alarms, security products must be installed in the correct spaces and tested frequently.
- Verify that security tools are operating in their most secure configuration, and that not a single part of a network is unprotected
- Consider deleting duplicative or unused apps to eliminate risky, unused services.
- Be mindful of where you permit remote help desk apps like TeamViewer. These are mainly targeted by threat actors to gain access to laptops/systems
- Enhance credential hygiene
- Audit credential exposure
- Reduce the attack surface
- Harden the cloud
- Prevent security blind spots
- Stop initial access
Summary
According to Microsoft, approximately 80% of the ransomware is due to network configuration errors.
Ransomware is a malware (malicious software) or a computer virus. It is designed to deny the access to file(s) by the user in the system.
Money is demanded by the hacker from the victim to give back the access.
Microsoft suggested various mitigation for these risks.


Pingback: Key Points In Web Applications That Should Be Focused On While Doing Manual Testing - JayateerthKatti.com